

Fully Homomorphic Training and Inference on Binary Decision Tree and Random Forest (European Symposium on Research in Computer Security(ESORICS) 2024) This paper introduces a new method for training decision trees and random forests using CKKShomomorphicencryption (HE) in cloud environments, enhancing data privacy from multiple sources. The innovative Homomorphic Binary Decision Tree (HBDT) method utilizes a modified Gini Impurity index (MGI) for node splitting in encrypted data scenarios. Notably, the proposed training approach operates in a single cloud security domain without the need for decryption, addressing key challenges in privacy-preserving machine learning. We also propose an efficient method for inference utilizing only addition for path evaluation even when both models and inputs are encrypted, achieving O(1) multiplicative depth. Experiments demonstrate that this method surpasses the previous study by Akavia et al.’s by at least 3.7 times in the speed of inference. The study also expands to privacy-preserving random forests, with GPU acceleration ensuring feasibly efficient performance in both training and inference. | |
| HEaaN-STAT: a privacy-preserving statistical analysis toolkit for large-scale numerical, ordinal, and categorical data (IEEE Transaction on Dependable and Secure Computing, 2023.)Statistical analysis of largescale data is useful as it enables the extraction of a large amount of information, despite its simplicity. Therefore, fusing and analyzing data from different security domains is an attractive and promising approach, unless it jeopardizes the privacy of the data in any security domain. In this study, we proposed the HEaaN-STAT toolkit that can efficiently fuse data from different domains to enable largescale statistical analysis while protecting data privacy. Moreover, we proposed an efficient inverse operation and a table lookup function for Cheon-Kim-Kim-Song (CKKS) encrypted data, as well as a data encoding method for counting encrypted data. Based on this, we proposed a method for generating a contingency table with a large number of cases and k-percentile for largescale data that is hundreds to thousands of times faster than the method proposed by Lu et al. in NDSS’ 17. The validity of the proposed toolkit was verified through practical use for business applications using real-world data. |
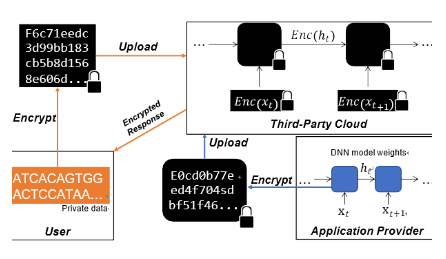 |
Privacy-Preserving Deep Sequential Model with Matrix Homomorphic Encryption (ASIACCS, 2022.) |
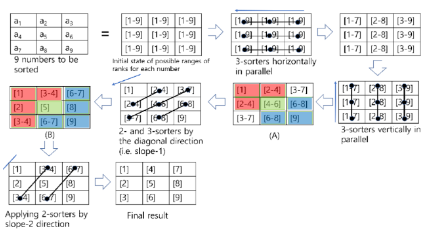 |
Efficient Sorting of Homomorphic Encrypted Data with k-Way Sorting Network
(IEEE Transactions on Information Forensics and Security, 2021.) We have found an efficient sorting method over encrypted data by applying k-way sorting network to the encrypted data by CKKS. With the help of efficient data comparison method and SIMD operations supported by CKKS HE, we could sort tens of thousands of data very quickly. |
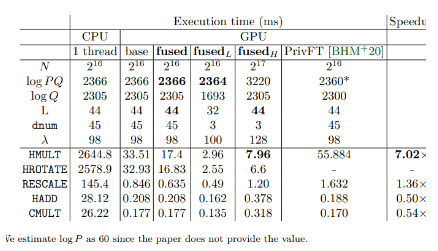 |
Over 100x Faster Bootstrapping in Fully Homomorphic Encryption through Memory-centric Optimization with GPUs. (In Proc. CHES 21, 2021.) |